Into the Nixverse
It seems like every time you think you know everything (orthere justis enough)to know about Linux, there's always something that catches you by surprise...
NixOS and the Nix package manager is software that allows you to configure a Linux system or shell environment in a declarative and therefore reproducible manner. In other words, your system can be completely immune from configuration drift. Nix also keeps track of a program's dependencies without mutating the global state of yourpackages, allowing for truly reproducible software builds and system isconfigurations. freeIn from side effects, such as when dependencies of one program are different than another, or when you update a package and the configuration file you've meticulously crafted is out of date. Also,addition, NixOS allows you to rollback to a previous system state, just in case something goes horribly wrong after you update things. Combined with version control with Git, NixOS lays the ground for a truly resilient system configuration for everything from Infrastructure as Code deployments to personal workstations.
An example system configuration file
# Createsconfiguration.nix
a# systemd-nspawnAn containerexample whichworkstation in turn runs podman containersconfiguration
{ config, lib, pkgs, ... }:
{
imports = [ ./hardware-configuration.nix ./additional-config.nix ];
boot.loader.systemd-boot.enable = true; # Enables the systemd bootloader
networking = { bridges.br0.interfaces# Enables networking using network manager
hostName = "nixos";
networkmanager.enable = true;
};
time.timeZone = "America/New_York";
users.users.sales = { # Creates a new user named sales
createHome = true;
extraGroups = [ "eth0" ];
bridges.br1.interfaces = [ "eth0"networkmanager" ];
};
containers.baobab = {
privateNetwork = true;
hostBridgesystem.stateVersion = "br0"; # Specify the bridge name
config = { config, pkgs, lib, ... }: {
virtualisation.containers.enable = true;
virtualization.oci-containers.backend = "podman";
virtualisation = {
podman.enable = true;
oci-containers.containers = {
nextcloud = {
image = "docker.io/syncthing/syncthing";
autoStart = true;
ports = [ "22000:22000" "22000:22000/udp" "8384:8384"];
extraOptions = [ "--pull=always"]
};
};
};
};
}24.11";
}All it takes to rebuild this system is putting the above Nix code into /etc/nixos/configuration.nix and executing nixos-rebuild switch. Yup, that's it! The Nix packages manager knows to install podman because of lines 13 and 14, and the container's configuration is located in lines 18-22. No need to mess around with packageapt, managersdnf or touch any config files. The Nix package manager will evaluate your configuration.nix file using the attributes (variables) you defined, compare it with the Nixpkgs repository to generate a build plan, and finally pulling pre-built binary packages from cache.nixos.org.
All of Nixos'NixOS' available packages can be found in https://search.nixos.org, and you can even follow along and see what each option does in the nixpkgs GitHub repository. I have also uploaded my own workstation's super riced-upfancy configuration onto the Grok ZoneGithub which you can find in this chapterhere.
Well thisactually...
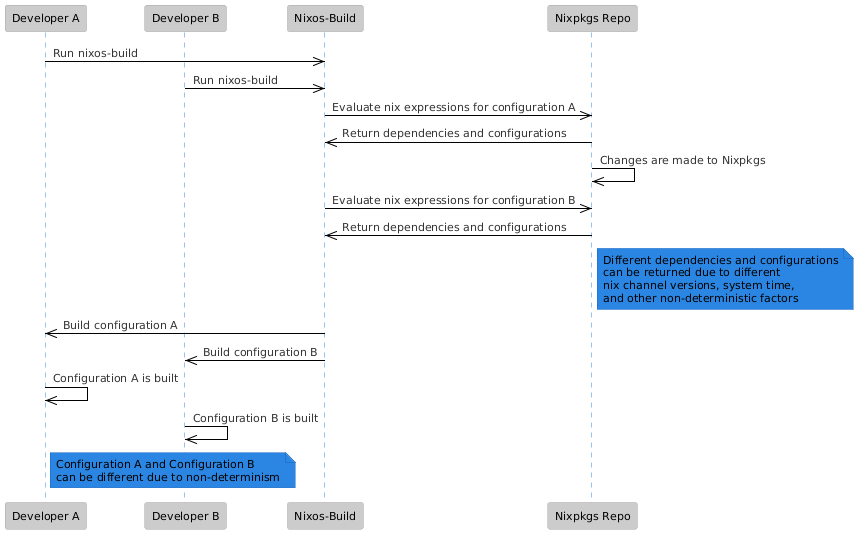
While hubbubusing also allows younixos-rebuild to publishbuild youra configurationssystem configuration can help ensure consistency, it does not guarantee consistency of a system's state across machines, as somethingthe calledbuild process is influenced by the state of the Nix package repository itself when the command was executed.
For example, if system A builds Firefox -> changes are committed to firefox in the Nixpkgs repository -> system B builds Firefox, the two systems are looking at two different versions of the Nixpkgs repository and will end up installing two different versions of Firefox.
This problem is solved by using Nix flakes, which allows you to,to write Nix code whose dependencies are version-pinned in a flake.lock file. Flakes also allow you to define a variety of options such as the previously mentioned NixOS configuration, a development shell for example,a sharereproducible yourdevelopment neovimenvironment, configbuild onlinechecks, andetc. (see the flake schema for options). As this is a big topic, I will have itto runwrite ona anyseparate otherpost systemregarding withNix justflakes oneanother command.
time.
...We'reSo, stillin not done here.summary,
Frankly, I'm still just a little Nix newbie and haven't even touched things like flakes and nix-writers. But even duringDuring my short time learning and using NixOS I've honestly been having a blast. It has honestly been verya refreshing to have something elseexperience to sinkwork thewith proverbiala teethLinux intodistribution inthat theprovides realmfor ofreproducibility, Linux.declarative configuration, and a strong focus on functional programming principles. I highly recommend Docker/Podman enthusiasts, DevOps engineers and experienced Linux users to give NixOS a whirl;whirl. itLike a new codebase, NixOS will take some time to get used to, but your future self that's upgradingbreaking or rebuildingupgrading your system will thank you.