Personal computing is half future-proof, half stuck in the past

Captain, I'm receiving a transmission from an unknown alien source.
Spock, can you decipher the message?
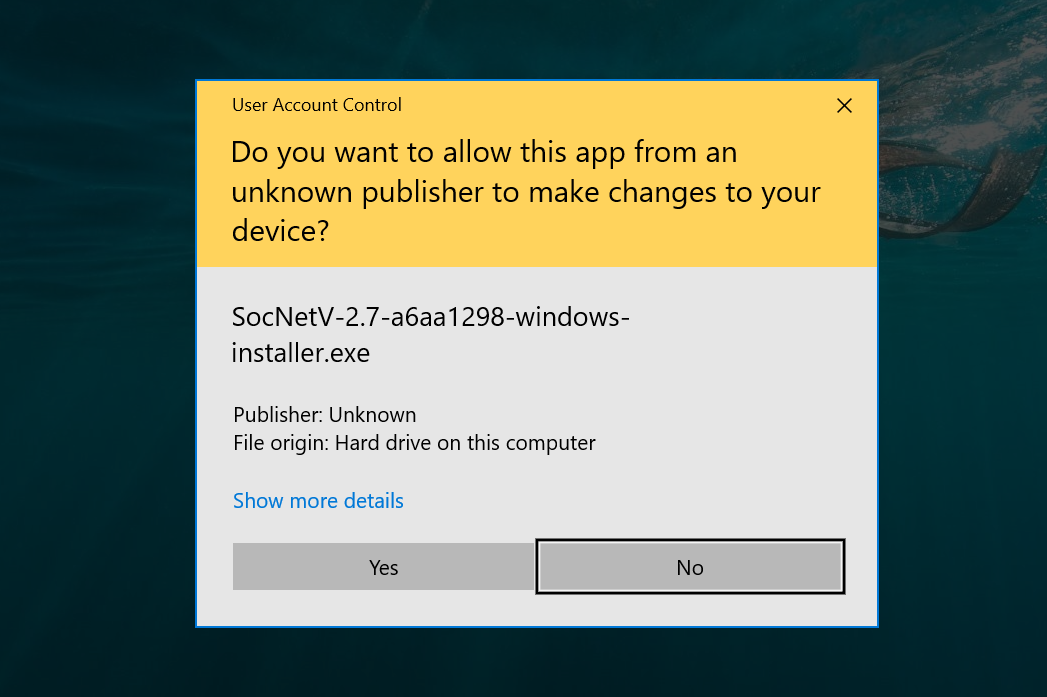
Yes captain, it's an executable file named 'word.exe'. I tried running it but application is not starting.
Err, let me try running it as an administrator.
(The Enterprise's computer systems blue screen and power off due to a poor sense of operations security)
In the realm of personal computing, there exists a strange difference in operation. On one hand, you have the mobile side, where permissions are explicitly granted to an application. Maybe that hilarious iBeer app, which turns your phone into a simulated pint glass, doesn't need access to your contacts... And, if any other app prompts you to access inappropriate permissions, you can simply deny it access. On the other hand, PC apps kind of just do whatever they feel like doing. Everything from your office programs to a funny purple monkey that dances around your desktop has essentially unfettered access to your user space.
Current Solutions
Applications that Windows and macOS users interact with nowadays are signed with a developer's private key when they are packaged, giving them the stamp of approval from Microsoft or Apple. And Microsoft and Apple are trustworthy, right? So... what's the issue?
Well, as it turns out these two companies don't really review the contents of the executables you decide to run. And for good reason- with the large amount of applications being created, it's probably impossible to review each one or even a majority of them. With that said, there are places like the Microsoft Store and the App Store where applications are reviewed before being published. However, even this is not foolproof plus you are always going to have some niche application that requires you to manually run or install an application outside of your curated app store.
But what about my anti-virus?
Anti-viruses are basically big tables of program signatures that try to identify malicious files. However, it isn't hard to make malicious applications that get missed by an antivirus, especially with the use of polymorphic code which allows an executable to change its appearance to anti-viruses.
So... what's the solution?
Well, to be clear the average user is probably smart enough to install applications from trustworthy sources. Or perhaps it is more truthful to say that search engines have become more cognizant as to verifying the links to websites to download software. Or perhaps anti-viruses are good at detecting malware in most cases. However, sticking to this paradigm of managing software is going to always be a cat and mouse game of creating novel, malicious software and detecting it.
On the contrary,allowing users to clearly grant permissions to applications has proven itself to be a good solution in the mobile operating system space. This is not without its issues though; for example, if permissions aren't granular enough, a developer might be forced to add an overly broad permission. It also requires the OS to have a secure enough sandbox, lest the applications would grant themselves permissions. However, with enough improvements such an access control system can, and has proved in mobile operating systems, to be a great security layer.
As an aside, it would also be nice if the applications people commonly use were all open source and auditable... including the operating system... but maybe I'm a little off my gourd.
What is your solution?
I'm a Linux user, and for the uninitiated Linux or more accurately GNU/Linux is essentially a very customizable customizable operating system, due to its highly documented and open source nature. An application for Linux called Flatpak allows for the sandboxing of user applications, while utilizing permission-based access similar to mobile applications. It's a wonderful way to install and use applications in a secure manner.
I'll explain in detail how I use flatpaks in my system in an upcoming blog post. For now, take a look at my dotfiles.
Happy computing!