Qubes OS
QubesOS is essentially a hypervisor that you can use as a desktop OS. Qubes allows you to run all of your programs inside of VMs, and streamlines the experience. Pretty neat, huh?
The beauty of Qubes is, besides being the a perfect OS for self-prescribed OCD people like myself, it is very functional. Qubes lets you perform tasks that may necessitate installing some of that undesirable closed-source software, such as TeamViewer or Citrix, within disposable virtual machines (VMs).
Every box with rounded corners represents a virtual machine. Glorious!
But how?
Qubes builds on top of the Xen hypervisor and presents it's own UI in the form of a desktop fedora installation. There, just like a normal Linux desktop, you can launch your applications.
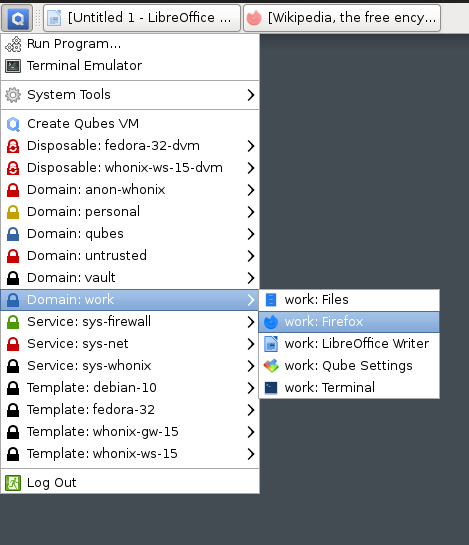
Hmm, this looks strange
The fact that Qubes runs all of your applications in a VM means that you actually need to first select the virtual machine, then select the application you would like to open. By isolating each application within its own VM, QubesOS prevents malware or vulnerabilities in one app from affecting others or the underlying system. It's like having separate, secure rooms for each activity, reducing the risk of a compromise spreading throughout your digital life.
Ideally, having every application be isolated into its own VM would be the best for security. However, this can be quite resource intensive especially for slower hardware. What Qubes does, then, is isolate applications into different security domains.
Qubes also does some fancy, arguably over-the-top things such as isolating usb and network devices from the host (seen as AdminVM aka dom0 in the diagram), in an effort to contain would-be exploitation attempts safely inside VMs.
Solutions to Qubes Quirks
- If your input devices are not directly connected to your computer's USB controller, you will need to remove the
usbcoredevice filter from your grub options:# /etc/default/grub GRUB_CMDLINE_LINUX= ... usbcore.authorized_default=0 ... # Remove the usbcore definition grub2-mkconfig -o /boot/efi/EFI/qubes/grub.cfg # Reconfigure the grub bootloader
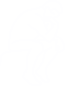
No Comments